Kernel DMA Protection
Kernel Direct Memory Access (DMA) Protection is a security feature in Windows designed to prevent unauthorized access to memory by external peripherals.
Kernel DMA Protection requires UEFI firmware support, and Virtualization-based Security (VBS) isn’t required.
Kernel DMA protection on or off?
Kernel DMA Protection offers enhanced security measures for the system compared to the countermeasures against BitLocker DMA attacks, all while preserving the usability of external peripherals.
Support for DMA remapping for graphics devices was introduced in Windows 11 with the WDDM 3.0 driver model, a feature not available in Windows 10.
Enumeration policy for external devices incompatible with Kernel DMA Protection
This policy aims to enhance security measures against external DMA-capable devices by offering increased control over the enumeration of such devices that may not support DMA Remapping or device memory isolation and sandboxing.
Note: This policy does not apply to 1394, PCMCIA or ExpressCard devices. The protection also only applies to Windows 10 R1803 or higher, and also requires a UEFI BIOS to function.
Note #2: More information on this feature is available at this link: Kernel DMA Protection for Thunderbolt? 3 (Windows 10) | Microsoft Docs.
Rationale for configuration
Device memory sandboxing enables the operating system to utilize a device’s I/O Memory Management Unit (IOMMU) to prevent unauthorized I/O or memory access by the peripheral.
If you don’t configure the setting, external devices that aren’t compatible with DMA-remapping won’t show up or work until you log in and unlock your user session. Once they’re recognized, these devices will keep working no matter if your session is active or not. However, devices that do support DMA-remapping will be quickly identified and their device memory will be protected.
DMA attack
DMA (Direct Memory Access) attacks refer to techniques used by attackers to gain unauthorized access to a system’s memory, bypassing traditional security measures and potentially compromising sensitive data or gaining control over the system.
A DMA attack takes advantage of the DMA functionality, which allows certain hardware devices to directly access the system’s memory without involving the CPU. Windows uses the system Input/Output Memory Management Unit (IOMMU) to block external peripherals from starting and performing DMA, unless the drivers for these peripherals support memory isolation (such as DMA-remapping).
Kernel DMA Protection safeguards solely against drive-by DMA attacks following the operating system’s initialization. It’s the responsibility of the system firmware/BIOS to protect against attacks via the Thunderbolt 3 ports during boot.
Examples of DMA attacks include:
IEEE 1394 (FireWire, i.LINK, mLAN commercial name) DMA Attack: Attackers can use IEEE 1394 device, such as an external hard drive or a malicious Firewire peripheral, to initiate DMA transfers and access the system’s memory directly. This attack has been demonstrated against various operating systems, including Windows, macOS, and Linux.
Thunderbolt DMA attack: An attacker can leverage the Thunderbolt interface, which also supports DMA, to gain unauthorized access to system memory. Thunderbolt devices can be used to initiate DMA transfers and potentially compromise the system.
GPU (Graphics Processing Unit) DMA attack: Modern GPUs have direct access to system memory through DMA for performance reasons. Vulnerabilities in GPU drivers or firmware could potentially allow attackers to gain control over the GPU and leverage its DMA capabilities to access or manipulate system memory.
Enable Kernel DMA Protection
Systems compatible with Kernel DMA Protection will activate the feature automatically, without any need for user or IT admin configuration.
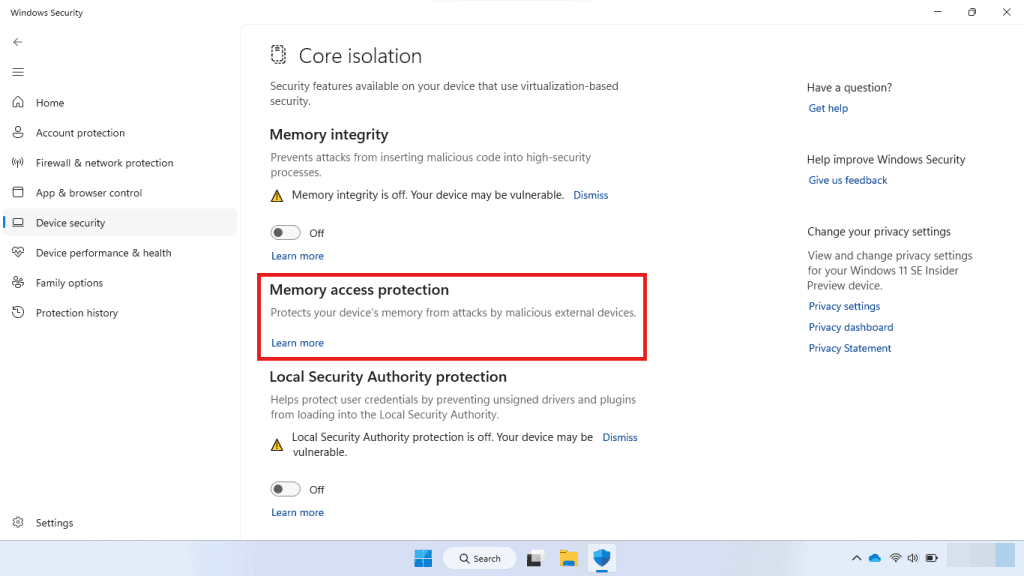
You can verify whether Kernel DMA Protection is enabled using the Windows Security settings.
- Open Windows Security.
- Select Device security > Core isolation details > Memory access protection
(reference: Microsoft, Kernel DMA Protection)
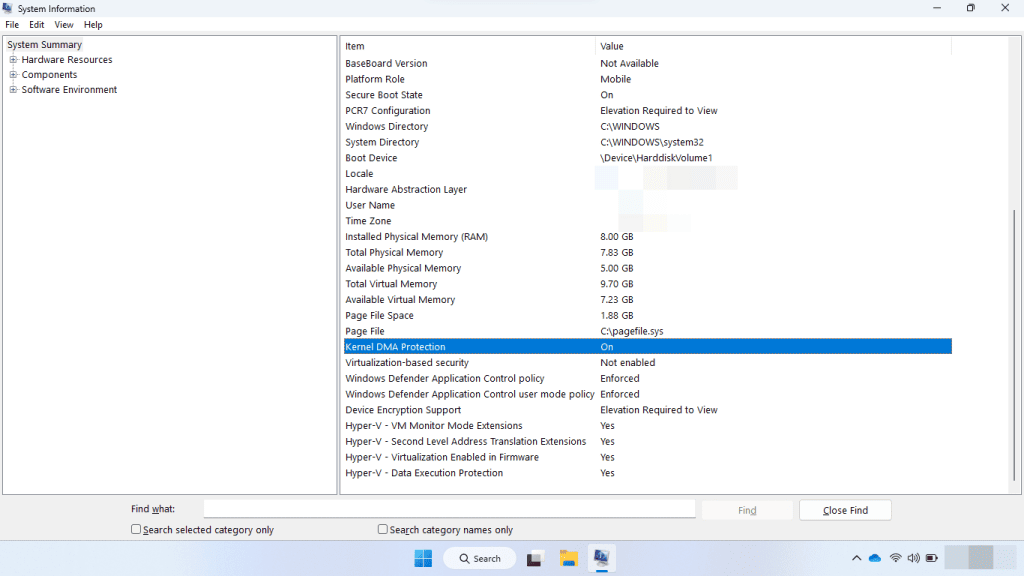
Alternatively, you can use the System Information desktop app (msinfo32.exe). If the system supports Kernel DMA Protection, the Kernel DMA Protection value will be set to ON.
(reference: Microsoft, Kernel DMA Protection)
If the current state of Kernel DMA Protection is OFF and Hyper-V – Virtualization Enabled in Firmware is NO:
- Reboot into UEFI settings
- Turn on Intel Virtualization Technology
- Turn on Intel Virtualization Technology for I/O (VT-d)
- Reboot system into Windows
Enable the external device enumeration policy
The External device enumeration policy controls whether to enumerate external peripherals that aren’t compatible with DMA-remapping.
The policy can be enabled by using:
- Group Policy: Administrative Templates\System\Kernel DMA Protection\Enumeration policy for external devices incompatible with Kernel DMA Protection
Enumeration policy for external devices incompatible with Kernel DMA Protection via GPO
This policy becomes active solely when Kernel DMA Protection is enabled and supported by the system. Note: It does not apply to 1394, PCMCIA, or ExpressCard devices.
Block all (0)
| Registry Hive | HKEY_LOCAL_MACHINE |
| Registry Path | Software\Policies\Microsoft\Windows\Kernel DMA Protection |
| Value Name | DeviceEnumerationPolicy |
| Value Type | REG_DWORD |
| Value | 0 |
Only while logged in (default) (1)
| Registry Hive | HKEY_LOCAL_MACHINE |
| Registry Path | Software\Policies\Microsoft\Windows\Kernel DMA Protection |
| Value Name | DeviceEnumerationPolicy |
| Value Type | REG_DWORD |
| Value | 1 |
Allow all (2)
| Registry Hive | HKEY_LOCAL_MACHINE |
| Registry Path | Software\Policies\Microsoft\Windows\Kernel DMA Protection |
| Value Name | DeviceEnumerationPolicy |
| Value Type | REG_DWORD |
| Value | 2 |
Disable Kernel DMA Protection
To establish the recommended configuration via GP, set the following UI path to Enabled: Block All:
| Computer Configuration\Policies\Administrative Templates\System\Kernel DMA Protection\Enumeration policy for external devices incompatible with Kernel DMA Protection |
Note: This Group Policy path may not exist by default. It is provided by the Group Policy template DmaGuard.admx/adml that is included with the Microsoft Windows 10 Release 1809 & Server 2019 Administrative Templates (or newer).
Hardening Kernel DMA Protection
Hardening Kernel DMA Protection refers to the process of enhancing the security of a system’s Direct Memory Access (DMA) by implementing measures to prevent unauthorized access to the system’s memory.
Automating the hardening process offers several advantages, making it the preferred approach for enhancing system security:
- Manual configuration is prone to human error, which can leave systems vulnerable if proper settings are not applied consistently across the infrastructure.
- Automation ensures that hardening measures like enabling IOMMU, disabling unnecessary DMA-capable interfaces, and applying least privilege mappings are implemented uniformly and reliably.
- Automated processes can be triggered during system provisioning, updates, or on a recurring schedule to maintain the desired security posture.
- Automation also simplifies the management and auditing of DMA protection policies, making it easier to validate compliance across a large number of systems.
Remember, hardening Kernel DMA Protection isn’t just an option, it’s an essential step in securing your digital domain. So, take charge and build a stronger, more resilient system today.