Distributed Denial of Service (DDoS) attacks are already 'permanent residents' in the cybersecurity statistics, but as time goes by their complexity, sophistication, and duration increase. Here are some interesting statistics on the DDoS attack:
- The frequency of DDoS attacks has increased more than 2.5 times over the last few years.
- The average size of DDoS attacks also increases and approaching to 1Gbps. Enough to take most organizations down.
- The average duration of the attacks continuously growing. In 2018 the first quarter attack time average was 95 minutes, comparing to 218 minutes in the fourth quarter.
- The 2018 fourth quarter witnessed the longest attack seen in recent years, lasting almost 16 days (329 hours).
- The cost of a DDoS attack averages between 20,000$-40,000$ per hour.
- Although the simple DDoS attack rate is starting to decrease, more complex attacks such as HTTP flood, remain popular, and their duration continues to increase.
- According to 2018 last quarter reports, the UDP flood attack vector increased significantly. SYN flooding is still the leading attack vector (58.2%).
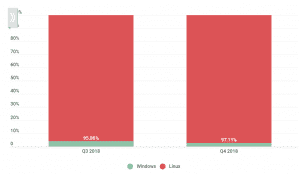
- Linux botnets are much more common than Windows botnets.
This blog post will cover:
Understanding the DDoS attack:
DDoS attack divides into three categories:
- Volume-based attacks– high traffic is used to bombarding the network bandwidth.
- Protocol attacks- focusing on exploiting server resources. A botnet is used to run a large number of scripts in the compromised server. The result is resources such as servers' memory or CPU get exhausted.
- Application attacks- focus on web applications. Considered to be the most sophisticated and serious type of DDoS attack.
DDoS attacks' malicious activity is generated from multiple sources, although controlled from a single point. This quality makes attack prevention extremely harder than attack distributed from a single point.
Another DDoS attack trend, that makes it even harder to prevent is the 'amplification' attacks trend. These attacks involve sending out small data packets to badly configured servers, which then respond by sending much larger packets to the targeted server that is under attack. One of the most common examples of this attack is a DNS amplification attack, where a 60-byte DNS request may result in a 4,000-byte response that is sent to the victim.
Popular DDoS attack types:
- SYN Flood- leverages TCP connection sequence weakness, know as a three-way handshake. The normal process is that after the host machine receives a synchronized (SYN) message to begin the 'handshake', it acknowledges the message by sending an acknowledgment (ACK) flag. The ACK flag is sent to the initial host which closes the connection. In an SYN flood, a spoofed message is sent, which prevents the connection from closing, shutting down the service.
- UDP Flood- The User Datagram Protocol (UDP) is a sessionless networking protocol. UDP flood target ports on the computer or network that has UDP packets. When the host searches for the application that supposes to listen to these ports, no source application is found.
- Smurf Flood- a Smurf Attack leverages IP and ICMP protocols, using a malware called 'smurf'. It spoofs the IP address and then uses the ICMP.
- Slowloris Attack- this attack uses minimal resources and targets the webserver. Once it connected to the target, it keeps the connection as long as possible with HTTP flooding.
- Application-level attack- this attack exploits vulnerabilities in applications. This attacks' goal is not to go after the entire server, but only after applications with known vulnerabilities.
- NTP Amplification- this attack exploits NTP servers (used to synchronized computer clocks) in order to overwhelm UDP traffic. This is an amplified reflection attack and there is a response from the server to a spoofed IP address. The response from the server is disproportionate to the original request, that's why this type of address can be devastating and high volume.
Optional way to detect DDoS attacks:
as mentioned before, the DDoS attack strategy is to make computer resources unavailable to its users. There may be a time gap between the beginning of the attack until it gets detected. The sooner the attack is detected, the better in terms of damage to the system. In order to detect it, you can use 'netstat' command in order to display protocol statistics and current TCP/IP network connections in the system.
Windows:
Login to your RDP server via RDP client, open the command prompt by visiting Start > Run > Type 'cmd' in the box. Type 'netstat -noa' in order to see all the connections.
noa:
n: displays active TCP connections. Addresses and port numbers are expressed numerically.
o: displays active TCP connections and includes the process ID for each connection. You can find the application based on the process ID in the Processes tab in Windows Task Manager.
a: display all active TCP connections and TCP & UPD ports on which the computer is listening.
When the statistics are displayed, look for the IP addresses which are having a maximum number of connections and block them using Personal Firewall.
Linux:
Log in the server via SSH.
Show source IP addresses and number of connections using:
# ss -tan state established | grep “:80\|:443” | awk ‘{print $4}’| cut -d’:’ -f1 | sort -n | uniq -c | sort -nr
Find the domains under the attack:
# for log in /var/www/vhosts/system/*/logs/*access*log; do echo -n “$log “; tail -n10000 “$log” | grep -c 203.0.113.2; done | sort -n -k2
Check number of connections, for possible syn-flood detection, in SYN_RECV:
# ss -tan state syn-recv | wc -l
In case of several IP addresses on Plesk, determine the target IP under attack:
# netstat -lpan | grep SYN_RECV | awk ‘{print $4}’ | cut -d: -f1 | sort | uniq -c | sort -nk 1
https://www.esecurityplanet.com/networks/how-to-prevent-ddos-attacks-tips-to-keep-your-website-safe