A new version of TLS was launched in 2018 - the TLS 1.3 protocol. TLS 1.3 aims to solve all of the problems facing its older version - TLS 1.2. While TLS 1.2 was a good choice for a TLS protocol until recently, but now, TLS 1.3 offers a better solution with a refreshing approach, especially for security-related matters. As configuring your systems to using only TLS 1.2 and above can be painful and cause production damage, so does the update for TLS 1.3. This is the main reason why a well-designed protocol like TLS 1.3 has yet to see extensive usage. However, updating your TLS protocol doesn’t have to be painful if using automated tools that can prevent outages and save you time and effort.
In this article you will learn:
- What is TLS protocol
- What is TLS 1.2 and its possible attack vectors
- About TLS 1.3 protocol
- TLS 1.2 vs. TLS 1.3
What is TLS?
Transport Layer Security (TLS) is a cryptographic protocol designed to provide secure communication between web browsers and servers. It is used in almost every app nowadays. Many IP-based protocols such as HTTPS, SMTP, POP3, and FTP support TLS. Secure Sockets Layer (SSL), on the other hand, is a protocol used to establish an encrypted link between web browsers and servers. It uses symmetric cryptography to encrypt the data transmitted. Encryption keys are based on shared secret negotiation at the beginning of any communication session. This secret negotiation is referred to as the TLS handshake.
The most widely used versions of TLS nowadays are TLS 1.0, TLS 1.1, and TLS 1.2. While TLS 1.0 & TLS 1.1 are known to be very vulnerable, the TLS 1.2 protocol is considered to be much more secure and is thus recommended for use. Furthermore, In October 2018, Apple, Google, Microsoft & Mozilla (responsible for Chrome, Edge, IE, Firefox, and Safari browsers) announced that by the first half of 2020, TLS 1.0 & 1.1 will be disabled by them. While that is a good move by them, the question is: What if TLS 1.2 is no longer as secure as we thought?
TLS 1.2:
TLS version 1.2 was released in 2008. It is currently the most widely implemented version of TLS. TLS 1.2 offers major improvements over the older version, TLS 1.1. The most essential improvement, however, is in the encryption protocol. TLS 1.2 allows the use of more secure hash algorithms such as SHA-256. In addition, it allows the use of advanced cipher suites that support elliptic curve cryptography. Up until recently, TLS 1.2 was considered fairly secure, but the discovery of new vulnerabilities, similar to the old TLS protocols' vulnerabilities, put TLS 1.2's reliability in question.
Zombie POODLE vulnerability in TLS 1.2:
We know about the Zombie POODLE attacks from five years ago which leveraged SSL 3.0 vulnerabilities. And apparently, they haven't really died.
Researchers have revealed two new vulnerabilities in the TLS 1.2 protocol which allows attacks similar to POODLE to breach it. The source of one vulnerability is in TLS 1.2's support for the outdated cryptographic method, cipher block chaining (CBC). Using the CBC method allows man-in-the-middle attacks (MITM) on users' encrypted web and VPN sessions. With some minor tweaking of the familiar POODLE attack, it is possible to hack systems that still make use of outdated crypto methods.
Another vulnerability was also found in TLS 1.2 which allows the GOLDENDOODLE attack to breach outdated crypto methods. GOLDENDOODLE is similar to, yet more powerful than the POODLE attack. It has more powerful and rapid hacking abilities, and even if a system has fully eradicated the POODLE flaw, it could still be vulnerable to GOLDENDOODLE attacks.
While this issue should have been resolved four or five years ago, the support for older protocols – which was included mainly to ensure that older legacy browsers and client machines won't be locked out of websites – means that the issue still remains. Meanwhile, those websites, operated mainly by government agencies and financial institutions, remain vulnerable.

TLS 1.3 takes a significant step forward in security when compared to TLS 1.2. It removes all primitive features that lead to weak configurations.
TLS 1.2 possible attack vector:
The new TLS 1.2 vulnerability, like the old POODLE, allows the attacker to gain access to encrypted blocks of data - and then gain exposure to plain text information - using side channels. The procedure is this: if the victim visits, for example, a non-encrypted website, malicious JavaScript is injected into the victim's browser. Once the browser is infected, a MITM attack is executed and the attacker can grab the victim's cookies and credentials from a secure web session.
TLS 1.3:
In addition to TLS 1.2's security issues, problems in performance and privacy were also noted in TLS 1.2. Therefore, a new version of TLS was launched in 2018 - the TLS 1.3 protocol. TLS 1.3 aims to address all of the problems facing TLS 1.2. Security-wise, TLS 1.3 completely abandons backward compatibility and has a completely new functional security design. TLS 1.3's security was designed from scratch, which allows it to perform the same functions as TLS 1.2, but with significantly improved resilience to attacks.
TLS 1.3 vs. TLS 1.2:
In August 2018, version 1.3 of the TLS protocol was released. The new version includes a lot of privacy, security and performance improvements. With TLS 1.3, encrypted connections are much faster and more secure than before. While high profile vulnerabilities were discovered in TLS 1.2, TLS 1.3 solves those issues and supports only state-of-the-art algorithms with no known vulnerabilities.
TLS 1.3 also provides additional privacy by encrypting more of the handshake to protect it from eavesdroppers.
Features removed from TLS 1.3:
- Static RSA handshake
- CBC MtE modes
- RC4
- SHA1, MD5
- Compression
- Regeneration
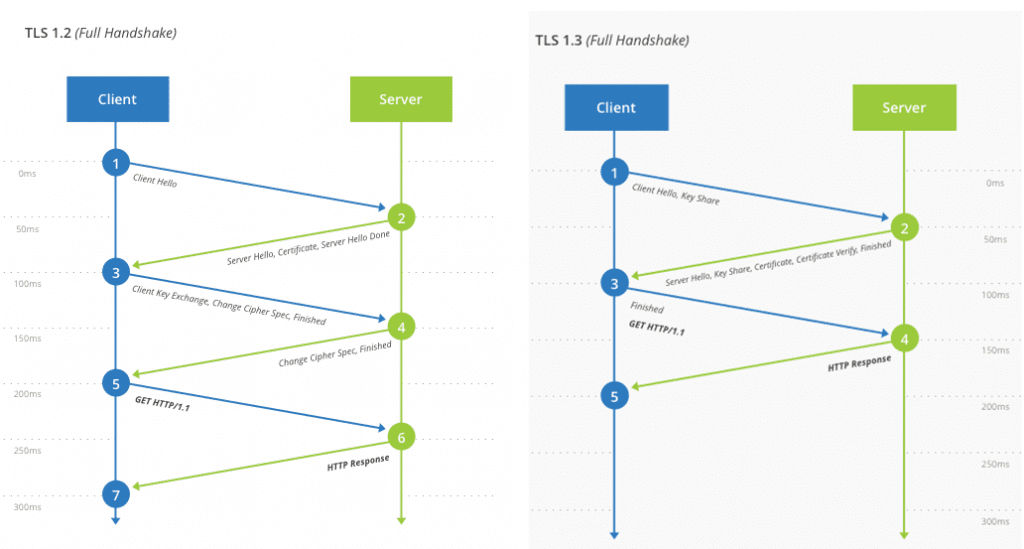
Security-wise, TLS 1.3 completely abandons backward compatibility, and has a completely new functional security design.
Bottom line:TLS 1.3 takes a significant step forward in enhancing security. It removes all primitive features that lead to weak configurations. TLS 1.3 prevents common SSL/TLS vulnerabilities such as DROWN, POODLE, SLOTH, CRIME, and more. We recommend to use assistive tools such as PowerShell, or other hardening automation platforms to help you increase IIS security.
References:
https://www.ietf.org/blog/tls13/
https://www.darkreading.com/application-security/tls-1-3-won-t-break-everything



