According to December 2018 Top 10 Malware report, WannaCry malware holds the dubious lead of malware breakdowns with 28%. WannaCry total damage is estimated by 4 billion $
But as WannaCry might be "old news" in malware breakdown reports, another malware, abusing the same SMB protocol, Brambul, is now in 3rd place with 12% of malware breakdowns. Although Brambul is also quite "old", this is her first entrance to the report, suggesting that it is still very relevant.
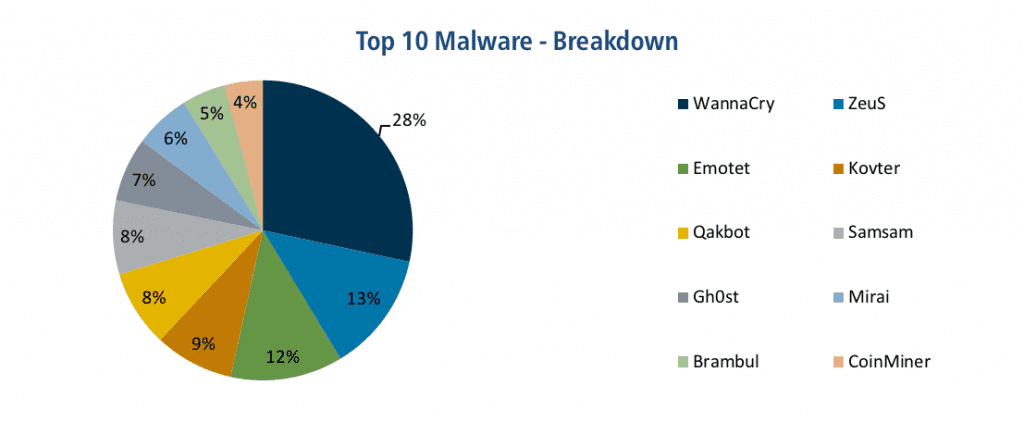
WannaCry first appearance was in May 2017, attacking Microsoft Windows operating systems by encrypting data and demanding ransom payments. Impact estimations were around 200,000 computers that were infected across 150 countries, including the National Health Services hospitals in England and Scotland. North Korea was blamed to be the directed responsible for the attack.
Critical hardening requirement from Microsoft- Disable SMB1
Although new in the Top 10 list, Brambul malware is even older than WannaCry and was first observed in 2009. Similar to WannaCry, Brambul malware also origins in North Korea.
Both WannaCry and Brambul are Server Message Block (SMB) worms. They spread through the SMB, which is Window's file- sharing protocol that enables shared access between users and network.
"The original SMB1 protocol is nearly 30 years old, and like much of the software made in the 80's, it was designed for a world that no longer exists. A world without malicious actors, without vast sets of important data, without near-universal computer usage" (MSFT Technet).

It is totally absurd that WannaCry malware is still causing so much damage these days, especially with such good solutions available in the market.
The absurd in this report is that in September 2016 the first security update regarding SMBv1 server was published by Microsoft, followed by another update only six months later. Check out our blog- post about mitigating WannaCry through SMBv1 disabling, published already in May 2017. So how come we are at 2019 and SMB worms are still so relevant?
Disabling SMBv1 is very complicated as it has dozens, if not hundreds of dependencies. An in-depth test must be performed before disabling it, and that might be the reason it still exists. Although Microsoft really wants organizations to get rid of it, the complexity in implementing those security updates might win in the battle between risks taking and efforts investment.
Letting an already solved vulnerability be so relevant and so harmful sounds unreal. Check out here how you can automate SMBv1 mapping and disabling with CalCom hardening automation learning capabilities.



