Kerberos Authentication Explained
Kerberos stands as the default authentication protocol facilitating secure service requests between trusted devices within a network. It has been an integral component of Windows Active Directory (AD) environments since the era of Windows 2000. When a user logs into their computer, Kerberos undertakes mutual authentication, ensuring both the user and the server validate their identities. Employing tickets instead of transmitting passwords directly over the network, Kerberos operates as a stateless authentication protocol.
Originating in the late 1980s, Kerberos emerged from MIT as a network authentication system designed for the Project Athena environment. Its primary objective was to furnish secure access to network systems while safeguarding against the exposure of passwords and sensitive data during transmission. By leveraging Kerberos, MIT aimed to thwart potential eavesdroppers from intercepting sensitive information. Kerberos has since progressed to its current version, V5 Release 1.21.2, initially published in 1993 as a proposed standard documented in RFC 4120.
Windows Server operating systems implement the Kerberos version 5 authentication protocol along with extensions supporting public key authentication, authorization data transportation, and delegation. The Kerberos authentication client operates as a security support provider (SSP), accessible through the Security Support Provider Interface (SSPI). The initial user authentication process seamlessly integrates with Winlogon’s single sign-on architecture.
The Kerberos Key Distribution Center (KDC) seamlessly integrates with other security services hosted on the domain controller within Windows Server. Utilizing the Active Directory Domain Services database, the KDC serves as the repository for security account information. For default Kerberos implementations within a domain or forest, Active Directory Domain Services serves as a prerequisite.
Throughout its evolution, Kerberos has undergone transformative iterations, notably with versions 4 and 5 marking significant milestones in its developmental journey. Exploring the disparities between Kerberos v4 and Kerberos v5 offers valuable insights into its evolution and enhanced functionalities.
Difference between Kerberos version 4 and 5
This comparison will highlight the advancements and improvements between Kerberos version 4 and Kerberos version 5 in terms of security, functionality, and overall design.
Kerberos v4 vs v5 Security Features:
Kerberos 4: K4 relies on DES (Data Encryption Standard) for encryption, which is considered less secure compared to modern encryption standards. It uses a symmetric key system where the Key Distribution Center (KDC) shares a master key with each client and server.
Kerberos 5: K5 improves security by using stronger encryption algorithms like AES (Advanced Encryption Standard). It introduces support for mutual authentication, integrity checking, and replay detection, enhancing overall security compared to K4.
Kerberos v4 vs v5 Encryption:
Kerberos 4: Primarily uses DES for encryption, which is now considered weak against modern attacks due to its small key size and vulnerability to brute-force attacks.
Kerberos 5: Supports stronger encryption algorithms such as AES, providing better security against attacks. It also supports pluggable encryption mechanisms, allowing for flexibility and future updates in cryptographic algorithms.
Kerberos v4 vs v5 Ticket Structure:
Kerberos 4: Uses a simpler ticket structure compared to K5. Tickets in K4 do not contain information about the user’s authorization data or support for renewable tickets, limiting its flexibility.
Kerberos 5: Introduces a more flexible and extensible ticket structure. Tickets in K5 contain additional information such as authorization data, allowing for more sophisticated access control mechanisms and support for renewable tickets, which improves usability and scalability.
· Protocol Improvements:
Kerberos 5: Introduces several protocol improvements over K4, including support for cross-realm authentication, support for pre-authentication mechanisms to prevent certain attacks like brute-force password guessing, and improved support for delegation and proxy services.
· Backward Compatibility:
Kerberos 5: Although K5 is not backward compatible with K4 due to significant changes in the protocol, most Kerberos implementations provide mechanisms to support both K4 and K5 clients and servers simultaneously. This allows for a phased migration from K4 to K5 while maintaining compatibility with existing systems.
· Interoperability:
Kerberos 5: Offers better interoperability with other authentication protocols and standards compared to K4. K5 supports mechanisms such as GSSAPI (Generic Security Services Application Programming Interface), which allows applications to use different security mechanisms transparently.
· Overall Security:
Kerberos 5: Provides significantly better security features and stronger encryption compared to K4. K5 addresses many of the security weaknesses present in K4 and is considered the more secure option for authentication in modern environments.
While Kerberos 4 served as a foundational authentication protocol, Kerberos 5 offers substantial improvements in security, flexibility, and interoperability. Organizations should prioritize migrating to Kerberos 5 to benefit from its enhanced security features and support for modern cryptographic algorithms.
What is Kerberos version 5 in network security?
The Kerberos V5 protocol provides a mechanism for mutual authentication between a client and a server before application data is transmitted between them. Kerberos V5 is composed of three exchanges:
- AS Exchange (Authentication Service Exchange)
- TGS Exchange (Ticket Granting Service Exchange)
- Service Exchange
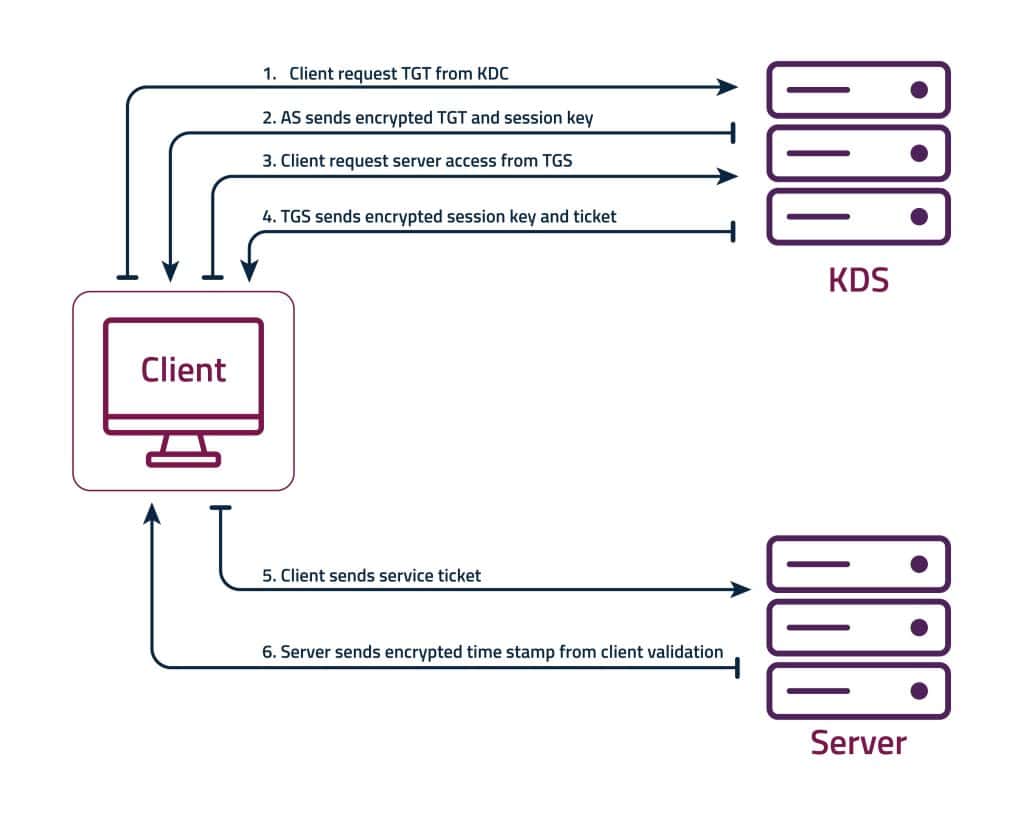
Kerberos 5 authentication involves several steps to securely authenticate a client to a server. Here’s a detailed overview of how Kerberos 5 authentication works:
- Client Authentication Request:
The client requests authentication by sending a request to the Authentication Server (AS), asking for a Ticket Granting Ticket (TGT) to access services.
- TGT Issuance by AS:
The AS verifies the client’s identity and issues a TGT encrypted with the client’s secret key, granting access to the Ticket Granting Server (TGS).
- Service Ticket Request:
The client requests a Service Ticket (ST) from the TGS for the desired service, presenting the TGT obtained earlier.
- ST Issuance by TGS:
The TGS verifies the TGT and issues an ST encrypted with the service’s secret key, allowing access to the requested service.
- Service Authentication:
The client presents the ST to the service. The service decrypts the ST, verifies the client’s identity, and grants access if authentication is successful.
- Secure Session Establishment:
Upon successful authentication, the client and service establish a secure session, allowing encrypted communication, often using keys derived from the exchanged tickets.
This concise representation captures the essential steps of Kerberos 5 authentication, from initial client authentication to the establishment of secure communication between the client and the service.
CalCom’s suite of server hardening tools offers comprehensive solutions for configuring, securing, and managing Kerberos authentication on Windows servers. By addressing the challenges associated with manual configuration, CalCom helps organizations enhance the security posture of their environments while reducing administrative overhead and ensuring compliance with security standards.