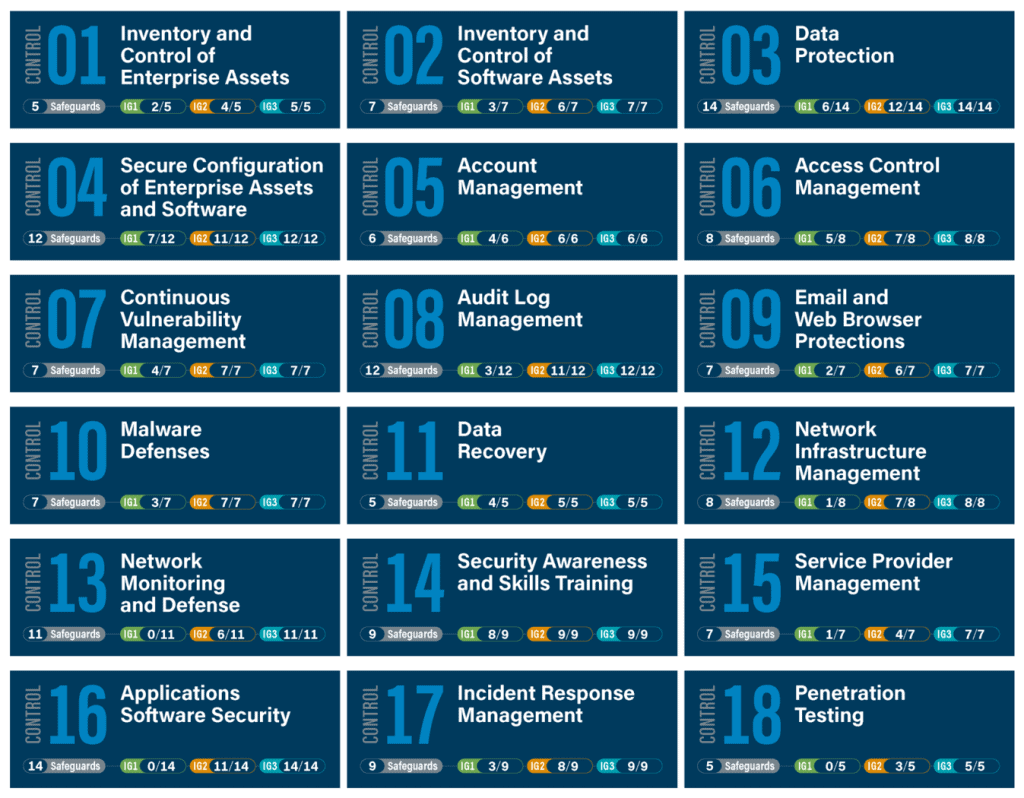
A list of 18 procedures (reduced from 20), or “controls,” recommended by the Center for Internet Security (CIS), must be followed to build an IT infrastructure resistant to cyberattacks. The CIS 4th Control advises to establish and maintain a secure configuration process for enterprise assets (end-user devices, including portable and mobile; non-computing/IoT devices; and servers) and software (operating systems and applications) (4.1). These CIS baselines also advise implementing system configuration management technologies that automatically impose and reinstall network configuration to devices at predetermined periods. To stop the attacks that take advantage of weak services and configurations, the CIS advises organizations to implement strict configuration and modification control procedures.
In CIS 8 the number of controls is reduced to 18 from 20 in CIS 7. CIS 8 contains 153 Safeguards, which were called sub-controls in CS7 and they were 171 sub-controls
Source: https://www.cisecurity.org/controls/implementation-groups/
Along with this request, the CIS baselines are a collection of hardening guidelines known as the CIS Benchmarks for various hosts, platforms, and operating systems. Despite being the industry norm for system hardening, research demonstrates that almost all firms fall short on more than 50% of the CIS Benchmarks conformance assessments. High-severity concerns contributed to over half of these losses. Most restrictions make system hardening a must. The depth that these CIS baselines offer make following them a hardship.
WHAT ARE THE CIS BENCHMARKS?
The CIS (Center for Internet Security) benchmarks are a set of technical guidelines and best practices designed for securing computer systems and networks to help organizations harden the security of their digital assets. They provide specific configuration recommendations and security controls for various operating systems, software applications, and devices.
These CIS baselines are developed by a volunteering community of cybersecurity experts and are continuously updated to address emerging threats and vulnerabilities via the CIS Workbench. They outline specific security settings, parameters, and hardening measures to protect systems from common attack vectors and ensure compliance with industry standards.

The following sections are found in the identically constructed rules. Here is the breakdown for setting: Ensure ‘Access this computer from the network’ is set to ‘Administrators, Authenticated Users, ENTERPRISE DOMAIN CONTROLLERS’ (DC only) (Automated)
- Headline: The advice is contained in the HEADLINE and the proposal’s significance level (L1). A proposal can be categorized as L1, which must be executed; L2, which can be executed at a later point of the hardening operation; or NA, which will be the least essential proposal.
- Profile Applicability: Which system component will be impacted by this policy is indicated by “profile applicability.”
- Description: A description of the rules of the setting.
- Rationale: The justification for establishing the regulation in the suggested manner.
- Impact: Any anticipated effect on your output.
- Audit: Audit suggestions for this rule.
- Remediation: Techniques you can use to make your machine comply with this guideline.
- Default value: Refers to the setting’s default value as it is initially configured.
- CIS Controls: With which this policy is associated.
According to newly identified intrusions, similar attacks, and system upgrades, the CIS Benchmarks are upgraded once or more per year.
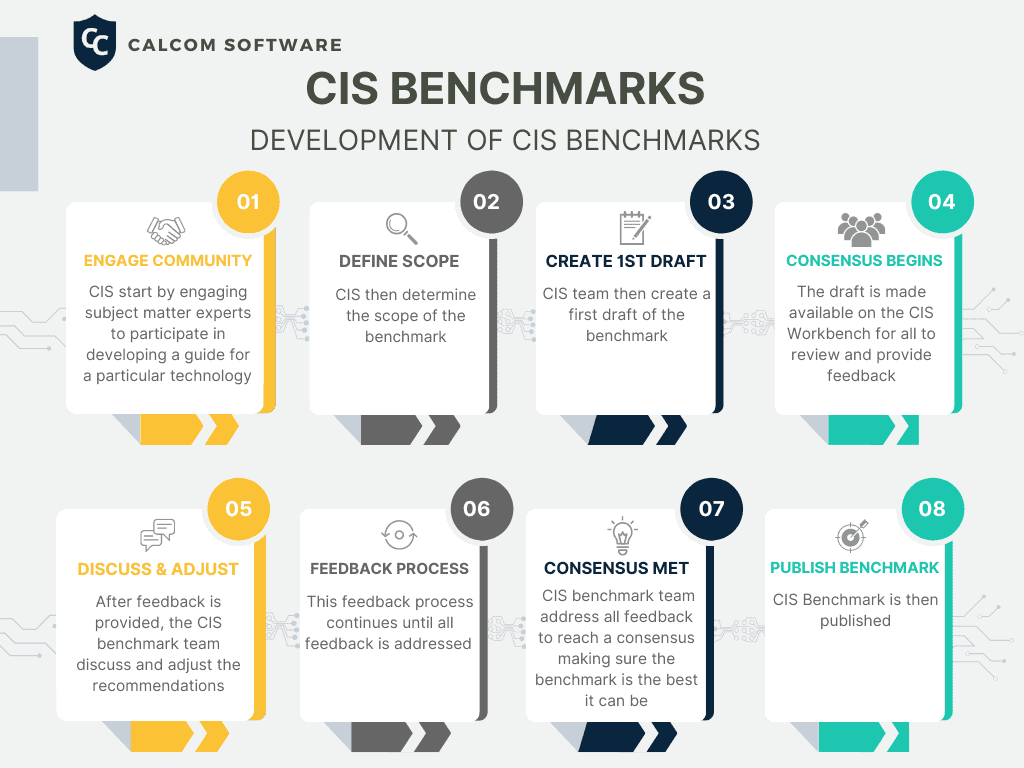
How the CIS Baselines Are Developed
The CIS baselines are a unique consensus based process led by a group of IT Experts and Cybersecurity Professionals from around the world. There are more than 12,000 professionals in the CIS Benchmark Communities collaborating on one benchmark. Each benchmark undergoes two phases of consensus review.
THE FIRST PHASE:
How a CIS Benchmark is Developed:
- Engage the Community: The process begins with the identification of a need for a new benchmark within the CIS community. This need serves as the catalyst for further exploration.
- Define Scope: CIS then determine the scope of the Benchmark
- Create a 1st Draft: CIS then create a first draft of the benchmark
- Consensus Begins: The draft is made available on the CIS Workbench for all to review and provide feedback
- Discuss and Adjust: After feedback is provided, the CIS benchmark team discuss and adjust the recommendations
- Feedback Process: This feedback process continues until all feedback is addressed
- Consensus Met: The CIS benchmark team incorporates all the feedback to achieve a consensus, ensuring the benchmark attains its highest level of quality
- Publish CIS Benchmark: After a consensus is met, the CIS Benchmark is then published
THE SECOND PHASE
In the second phase after the benchmark has been published, the consensus team reviews the feedback from the internet community for incorporation into the benchmark.
CIS Benchmark Levels
CIS benchmarks provide levels of security settings known as configuration profiles. These Levels are:
Level 1 This level offers basic security recommendations and requirements that can be configured on any system and should cause little or no interruption of service or reduced functionality.
Level 2 This level recommends a more stringent security setting that includes additional security settings and configurations that provide increased security measures and reduce the potential attack surface.
STIG (replaces what was Level 3) profile includes additional requirements from the STIG that were not covered in the Level 1 and Level 2 profiles.
Users who apply CIS baseline recommendations and require STIG compliance can easily bridge the gaps between the original CIS Benchmark profiles and STIGs by utilizing the three available profiles. All CIS benchmarks are freely available as PDF downloads from the CIS website.
WHY YOU SHOULD USE THE CIS BENCHMARKS?
The standard setup of the operating systems, as they are shipped from the vendor, prioritizes usability over security. Operating systems are thus highly susceptible to cyberattacks if security precautions aren’t taken. Attackers frequently penetrate an organization’s IT network, distribute malware, and do significant harm by making use of the threat landscape. For instance, the Server Message Block (SMB) worm WannaCry, which initially surfaced in May 2017, makes use of such a compromise to get access to the network and spread itself. Additionally, despite the fact that Microsoft delivered the appropriate security upgrades in 2016 and 2017, the WannaCry malware and other SMB worms like Brambul malware still inflict daily losses of thousands of dollars. Another popular target is the RDP protocol that can be significantly more secure once proper hardening actions are implemented.
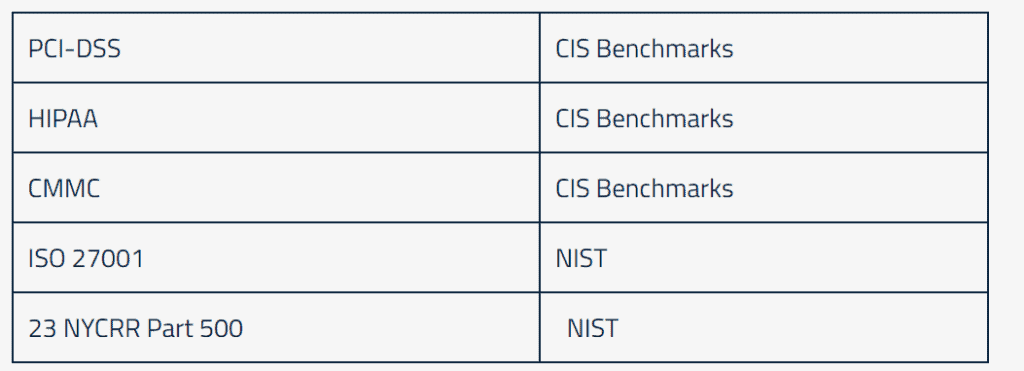
Restrictions must also be taken into account to limit organizational connect surface when determining whether or not to use CIS baselines. It is accurate to claim that practically all significant regulations directly or indirectly call for CIS basline adherence. Indirect means that specific laws demand adherence to other frameworks, such as the NIST Cybersecurity Framework, but these frameworks make reference to the CIS Baselines.
These regulations and frameworks each have their specific objectives and requirements, however, they often overlap or can be used in conjunction with each other to achieve comprehensive cybersecurity and compliance. Organizations often review multiple frameworks to ensure they fulfill the requisite requirements and adhere to established best practices and compliance.
HOW TO USE CIS BENCHMARKS:
The baseline of a CIS Benchmark is to assist businesses in “hardening” existing systems, which means safeguarding their configurations. One of the most challenging steps toward establishing a hardened infrastructure is putting the CIS baselines into practice.
There are two options for implementing CIS baselines:
Manual Implementation: This option involves downloading the CIS Benchmark PDF and manually implementing the suggested configurations. This approach is labor-intensive and challenging to ensure ongoing compliance, especially as configurations change and new assets are added.
Automated Solution: Most organizations opt for an automated CIS benchmark tool to simplify the implementation process. Using an automated solution makes it faster and easier to achieve and maintain compliance with the CIS benchmarks.
TOOLS TO IMPLEMENT CIS BENCHMARKS?
Scanners and Assessment Tools
Scanners and Assessment tools will indicate your CIS Benchmark compliance posture. When they are used they indicate the gap between your current policy and the CIS Benchmarks but do not provide any solution for overcoming this gap. You will have to test and enforce the changes to improve your compliance posture. CIS offers its own developed scanner - the CIS CAT.
Hardening Automation Tools
Hardening automation tools streamline the process of hardening systems by automating repetitive and time-consuming tasks. They can quickly apply security configurations, saving significant manual effort and reducing the chances of human error. When hardening, the most time consuming and inefficient use of resources is monitoring potential drifts. The largest advantage of hardening automation tools is that they eliminate the need to check what will be the impact of each configuration change on your network.
Hardening automation tools should offer the following solution:
-
- Scan to discover the gap between your current policy and your desired policy.
- Learn the network and indicate what will be the impact of each configuration change.
- Implement the new policy directly on production without testing or breaking anything.
- Monitor, control and prevent configuration changes, all from a single point of control.
CHS by CalCom is a server hardening automation tool. CHS learns the production environment and analyzes the impact of every configuration change. Thereby eliminating the need for lab testing and allowing the CIS baselines to be implemented directly on the environment without the risk of production outages. Learn more about CHS benefits.
Configuration Management Tools
Configuration management tools are not necessarily specific for security purposes, but they allow implementation of configuration changes on an infrastructure. These tools are relevant only after you scanned and found the gap between the policy and the baseline of the CIS Benchmark and test the predicted impact of each configuration change.