Open Source Hardening Explained
OS hardening refers to the process of enhancing the security of an operating system by implementing various measures and practices to minimize vulnerabilities and strengthen its resistance against potential cyber threats and attacks. This involves configuring the OS settings, applying security patches, disabling unnecessary services, and implementing access controls to create a more robust and secure computing environment.
An open source technology does not gain value through minimal and sporadic contributions. Open source projects are developed in public and provide an opportunity for rapid feedback from a wider audience. This means that substantial effort and strategic planning are essential components of this process.
Homeland Open Source Technology (HOST) Initiatives
Numerous inventive security solutions offered by open source software (OSS) remain untapped by the U.S. government. OSS refers to software for which the source code is accessible, allowing for its use, modification, and distribution. Dynamic OSS projects yield swift advancements and promote inclusive development, rendering them more adaptable to specialized demands. In cases where adjustments are necessary, the code can be accessed and modified accordingly. This adaptability, in conjunction with the rapid pace of innovation, positions open source security technology as a crucial source of solutions and we'll be discussing open source security for hardening.
The Homeland Open Source Technology (HOST) initiative strives to enhance the government’s utilization of OSS. According to a study carried out by Red Hat, a significant 75% of IT leaders expressed a strong sense of importance regarding enterprise open-source software. In 2006 The Department of Homeland Security provided US$1.24 million in funding for assorted open source security audit initiatives. The federal government expected that its Vulnerability Discovery and Remediation, Open Source Hardening Project would facilitate the construction of an automated vulnerability detection system capable of performing daily security audit scans of source code contributed to various open source projects.
Vulnerabilities in Open Source
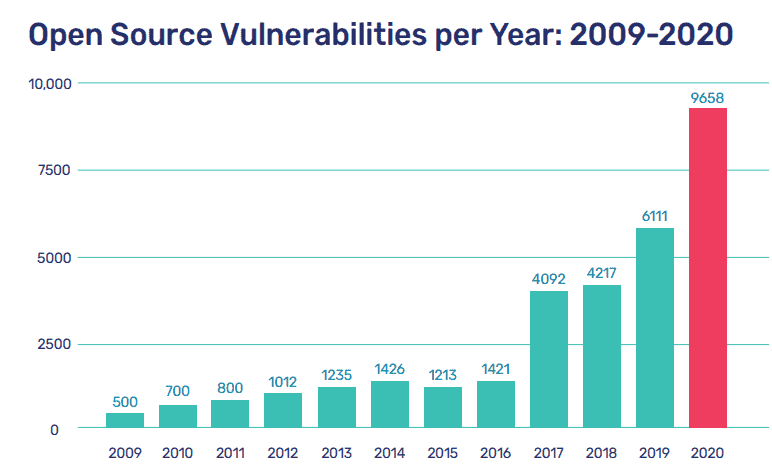
Open source vulnerabilities encompass pieces of code that have either been written with errors that can be exploited by hackers, or they consist of functionalities enabling attackers to execute harmful actions in manners unintended by the code’s original author. These vulnerabilities have the potential to impact the confidentiality, integrity, or availability of both the system and its associated data. Notably, an unprecedented volume of novel open source security vulnerabilities was disclosed in the year 2020. Some of these vulnerabilities might persist for more than four years prior to being identified.
Mend.io published a report discussing the most common CWEs in open source vulnerabilities in 2020 and the programming language with the highest number of such vulnerabilities among the top languages are notable aspects for consideration.
(Source: Mend.io, The State of Open Source Security Vulnerabilities (Annual Report 2021))
Some of the common vulnerabilities found in open-source projects include:
Code Flaws: Errors or mistakes in the code can lead to vulnerabilities. These can range from simple syntax errors to logic flaws that attackers can exploit.
Lack of Input Validation: Failing to properly validate and sanitize input data can allow attackers to inject malicious code or execute unintended actions.
Insecure Dependencies: Open-source projects often rely on external libraries and components. If these dependencies have security vulnerabilities, they can be exploited in the main project.
Weak Authentication and Authorization: Inadequate user authentication and authorization mechanisms can lead to unauthorized access and privilege escalation.
Insecure Configuration: Incorrect or default configurations can create security holes. This can include leaving sensitive information exposed or allowing unnecessary services to run.
Buffer Overflows: Poorly managed memory handling can lead to buffer overflows, where attackers can overwrite adjacent memory with malicious code.
Cross-Site Scripting (XSS): Improper handling of user-generated content can allow attackers to inject malicious scripts into web applications, affecting other users who access the content.
SQL Injection: Insufficient input validation can enable attackers to manipulate database queries, potentially gaining unauthorized access to the database.
Cross-Site Request Forgery (CSRF): Inadequate protection against CSRF attacks can allow attackers to perform actions on behalf of an authenticated user without their consent.
Security Misconfigurations: Misconfigured security settings, permissions, or network settings can create openings for attackers.
Outdated Software: Failure to keep software up to date with security patches can leave systems vulnerable to known exploits.
Insufficient Logging and Monitoring: Inadequate logging and monitoring make it harder to detect and respond to security incidents.
Hardening Best Practices for Open Source Projects
Hardening an open-source project involves implementing a series of security measures to enhance its resilience against potential threats and vulnerabilities. Here’s a general roadmap for best practices when hardening an open-source project:
Code Review and Vulnerability Assessment:
- Begin by conducting a thorough code review to identify any existing vulnerabilities or weaknesses in the project’s source code.
- Utilize automated tools, such as CalCom’s Hardening Suite (CHS) to detect common coding errors and security issues.
Patch Management:
- Keep the project’s dependencies and libraries up to date by regularly applying security patches and updates.
- Monitor security advisories for the software components used within the project and promptly apply recommended fixes.
- Securely configure the project’s settings and parameters to minimize potential attack surfaces.
- Disable unnecessary features and services that could introduce security risks.
Access Control and Authentication:
- Implement strong access controls, ensuring that only authorized users can access sensitive parts of the project.
- Enforce proper authentication mechanisms, such as multi-factor authentication, to prevent unauthorized access.
Input Validation and Sanitization:
- Validate and sanitize all user inputs to prevent injection attacks, cross-site scripting (XSS), and other common web vulnerabilities.
- Use secure coding practices to handle user data safely.
Encryption and Data Protection:
- Utilize encryption for sensitive data at rest and in transit, using appropriate encryption algorithms and key management practices.
- Implement secure protocols, such as HTTPS, to safeguard data during transmission.
Error Handling and Logging:
- Implement proper error handling to prevent information leakage that could aid attackers.
- Set up robust logging mechanisms to track and analyze potential security incidents.
Regular Security Audits and Penetration Testing:
- Conduct regular security audits and penetration testing to identify potential vulnerabilities and weaknesses.
- Engage security professionals to perform controlled testing and assessment of the project’s security posture.
Community Collaboration and Disclosure:
- Encourage collaboration within the open-source community to allow security experts to contribute insights and fixes.
- Establish a responsible disclosure process for reporting and addressing security vulnerabilities.
Documentation and Training:
- Provide clear and comprehensive documentation on secure deployment, configuration, and usage of the project.
- Offer training to users and contributors to ensure they understand and adhere to security best practices.
Continual Monitoring and Updates:
- Continuously monitor the project’s security posture and adapt to evolving threats and vulnerabilities.
- Regularly release updates and patches to address newly discovered security issues.
Hardening an open-source project requires a proactive and holistic approach to security, involving a combination of code-level enhancements, configuration adjustments, and collaborative efforts within the community.