What is IPv6 used for?
Internet Protocol version 6 (IPv6) is a network layer protocol that facilitates communication across the internet by assigning unique IP addresses to each device for identification and location purposes. With the onset of the digital era in the 1990s, the limitations of IPv4 addresses in accommodating the escalating demand became evident. Consequently, the Internet Engineering Task Force (IETF) embarked on developing the next-generation internet protocol, leading to the emergence of IPv6. Initially designated as a draft standard by the IETF in December 1998, IPv6 attained approval as an internet standard for global deployment on July 14, 2017.
Given that the majority of privately managed enterprise networks typically rely on private IPv4 addressing, the necessity for IPv6 utilization is often minimal. Disabling IPv6 components in such networks presents an opportunity to diminish a potential attack surface, which may otherwise be challenging to monitor effectively. Thus, it is recommended to configure IPv6 to a Disabled state when its functionality is not required.
Reasons to Disable IPv6
Given that most privately operated networks do not require IPv6 due to the availability of private IPv4 addressing, disabling IPv6 components eliminates a potential attack vector that is more challenging to monitor traffic on. Consequently, we advise setting IPv6 to a disabled state when it is not being used.
The security of a network greatly depends on the network architecture and the expertise of those responsible for configuring and managing its IPv6 implementation. Consequently, the security stance of an IPv6 implementation may vary significantly as the NSA states in their IPv6 Security Guidance.
Disabling IPv6 on Windows servers or client machines is a decision often made by system administrators for various reasons:
Compatibility Issues:
Older hardware or software may not fully support IPv6, leading to compatibility issues or reduced performance. Maintaining IPv4 compatibility can ensure seamless operation with existing infrastructure.
Network Management and Monitoring:
Some administrators may be more accustomed to managing and monitoring IPv4 networks. Familiarity with IPv4 tools and configurations can streamline network management processes, especially concerning legacy systems.
VPN and Firewall Configuration:
Certain VPN and firewall setups might not be optimized for IPv6, potentially compromising security and performance. Utilizing IPv4 can mitigate compatibility concerns and ensure consistent network operation.
Security Risks:
While IPv6 offers enhanced security features, improper configuration can expose networks to new vulnerabilities. The expansive address space and auto-configuration features in IPv6 may facilitate reconnaissance activities and exploit security weaknesses if not appropriately secured.
Complexity:
IPv6 introduces greater complexity compared to IPv4, particularly in address structure and management. This complexity can pose challenges for administrators and increase the risk of misconfigurations, leading to security vulnerabilities or performance degradation.
Dual-Stack Challenges:
Implementing both IPv4 and IPv6 (dual-stack) can complicate network management and security. Maintaining separate policies, rules, and configurations for each protocol increases the likelihood of misconfigurations and potential security risks.
By disabling IPv6, administrators aim to mitigate these concerns and ensure optimal performance, security, and manageability within their network environments.
How to disable IPv6
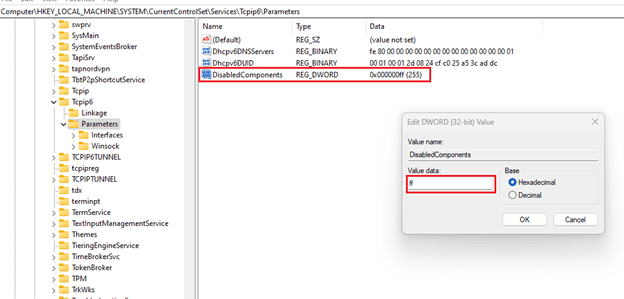
To disable IPv6 in Windows server/client machines admins need to ensure that TCPIP6 Parameter ‘DisabledComponents’ is set to ‘0xff (255)’ in OS's registry settings. This can be done using command line feature or manually.
Use the registry key to configure IPv6
The IPv6 functionality can be configured by modifying the following registry key:
- Location: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters\
- Name: DisabledComponents
- Type: REG_DWORD
- Min Value: 0x00 (default value)
- Max Value: 0xFF (IPv6 disabled)
By default, Windows enables the 6to4 tunneling protocol when an interface is allocated a public IPv4 address, defined as any IPv4 address outside the ranges 10.0.0.0/8, 172.16.0.0/12, or 192.168.0.0/16. The 6to4 protocol automatically assigns an IPv6 address to the 6to4 tunneling interface for each address, dynamically registering these IPv6 addresses on the designated DNS server. However, if this automatic behavior is undesired, it is advisable to disable IPv6 tunnel interfaces on the affected hosts. This step allows administrators to maintain control over IPv6 address assignment and DNS registration, aligning network configurations with specific requirements and preferences. Disabling the IPv6 tunnel interfaces ensures that IPv6 address assignments and DNS registrations adhere to the network’s desired policies and configurations, enhancing network management and security practices.
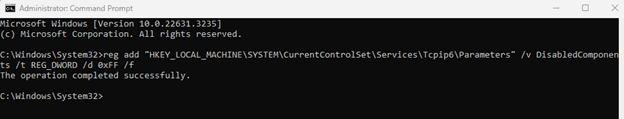
You can follow these steps to modify the registry key using command line:
- Open the Command Prompt window as an administrator.
- Run the following command:
reg add “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters” /v DisabledComponents /t REG_DWORD /d 0xFF /f
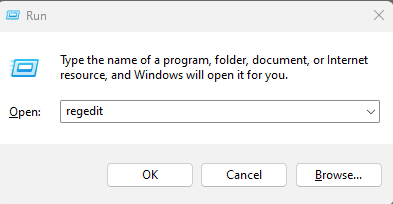
This can also be done by manually editing the registry value. To do that:
- Open Run using Ctrl + R button.
- Type regedit to open registry editor.
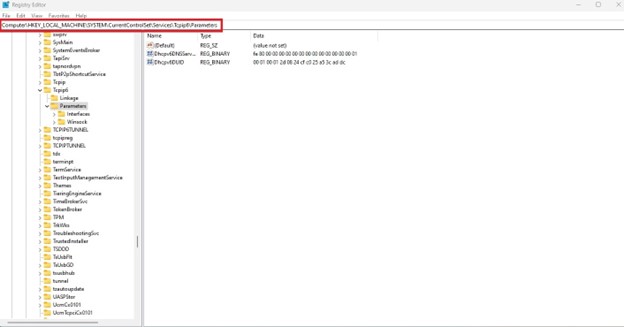
3. In the registry editor navigate to the following location;
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters
4. Right click on the empty space in the left window of the registry editor and click on New > DWORD (32-bit) Value.
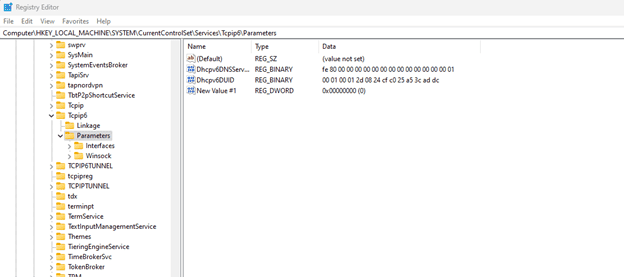
5. An entry named as "New Value #1" will be created.
6. Right click on this new entry and click on rename. Type the name as "DisabledComponents".
7. Double click on this new entry and you will see a dialogue box opened. Enter the value as ff and then click OK.
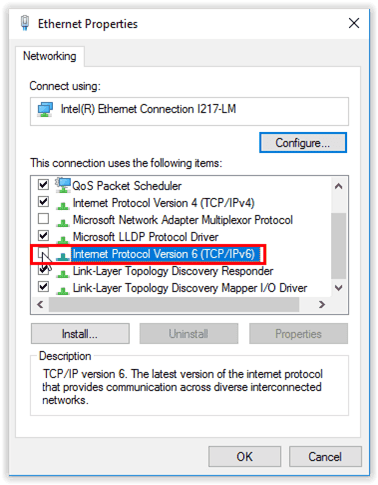
Using GUI method
Disabling IPv6 is not supported anymore using GUI method is not supported by Microsoft. This registry value doesn’t affect the state of the following check box. Even if the registry key is set to disable IPv6, the check box in the Networking tab for each interface can be selected. This is an expected behavior.

Consequences of disabling IPv6
Disabling IPv6 on Windows servers and clients can be a strategy to mitigate potential security risks by reducing the attack surface, given that IPv6 is not widely utilized in many networks. However, such a measure comes with several considerations.
One notable drawback is the potential for application compatibility issues, as some services and applications may rely on IPv6 functionality. Disabling IPv6 may pose challenges for future-proofing, as IPv6 is the future of Internet addressing and its adoption is gradually increasing.
Interoperability with networks and systems that do utilize IPv6 could become problematic, potentially hampering communication and collaboration. From a diagnostic and troubleshooting standpoint, disabling IPv6 may complicate efforts to identify and resolve network issues involving IPv6 components. Moreover, security implications persist, as disabling IPv6 alone does not address other potential vulnerabilities in the network stack. Lastly, managing updates and patches may require additional attention, as updates related to IPv6 functionality may need to be carefully monitored or managed.
Therefore, to disable IPv6 can reduce the attack surface, it should be part of a broader security strategy, carefully weighed against its potential impact on compatibility, interoperability, and future network requirements.
Disable IPv6 with Automated Configuration Hardening
The decision to disable IPv6 entails a delicate balance between its benefits and drawbacks. While disabling IPv6 can reduce the attack surface, simplify network management, and address compatibility issues, it may also hinder future-proofing efforts, limit interoperability, and complicate troubleshooting processes.
CIS Benchmark 18.5.19.2.1 Disable IPv6 for remediation states to establish the recommended configuration, set the following Registry value to 0xff (255) (DWORD):
|
Note: This change does not take effect until the computer has been restarted
Note #2: Although Microsoft does not provide an ADMX template to configure this registry value, a custom .ADM template (Disable-IPv6-Components-KB929852.adm) is provided in the CIS Benchmark Remediation Kit to facilitate its configuration. Be aware though that simply turning off the group policy setting in the .ADM template will not “undo” the change once applied. Instead, the opposite setting must be applied to change the registry value to the opposite state.
In the absence of an automated hardening solution, an enterprise organization managing numerous servers would be required to manually disable IPv6 configuration. However, this manual approach poses challenges, demanding careful consideration of factors such as network requirements, security priorities, and long-term goals.
Automated configuration hardening is preferable in such scenarios due to its efficiency, scalability, and ability to ensure consistent configuration across the network, thus streamlining management and reducing the risk of human error. By adopting automated solutions, organizations can effectively navigate the complexities of IPv6 management while aligning with their broader operational objectives.