What is Print Spooler?
Print Spooler is a component integrated into the Windows operating system, designed to temporarily hold print jobs in the computer’s memory until the printer is prepared to execute them.
How Print Spooler works
The administration of printing encompasses tasks such as acquiring the appropriate printer driver’s location, loading said driver, converting high-level function calls into a print job, arranging the print job for execution, and more. On all Windows platforms, the print spooler executable file (spoolsv.exe) is loaded by default upon system startup.
Examples where Print Spooler is required for operations:
- When using Citrix services.
- Fax servers.
- Any application that requires virtual or physical printing of PDFs, XPSs, etc. For example, billing services, and wages applications.
How to fix printer spooler
Here are three simple steps that will demonstrate restarting the print spooler, which could help resolve printer spooler error:
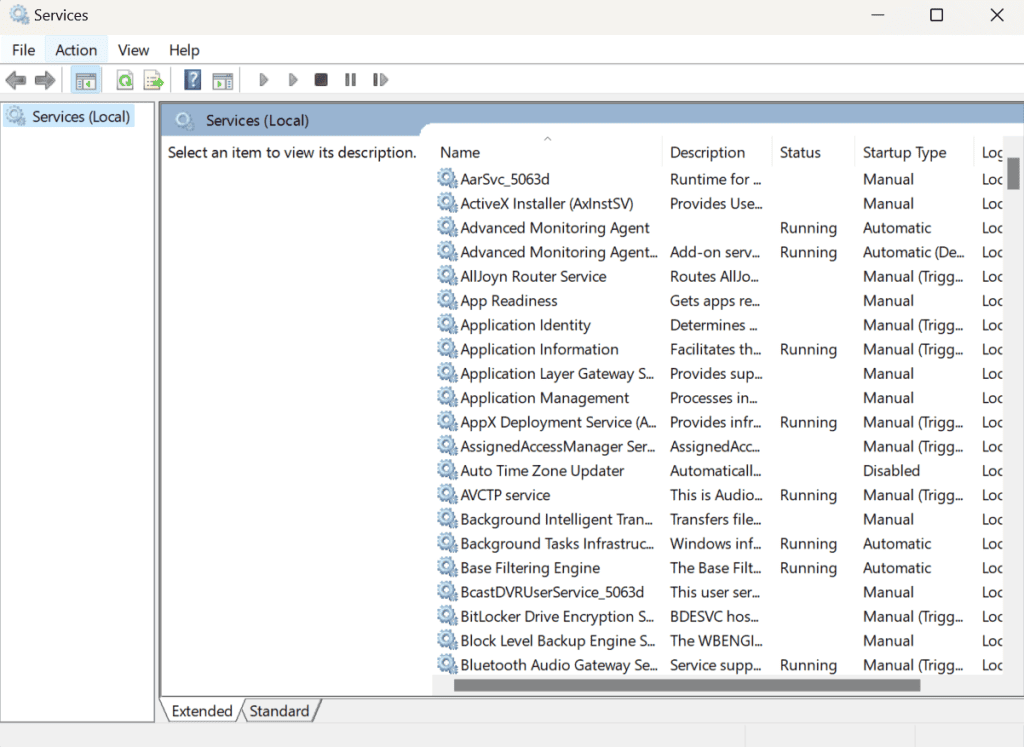
- Hover the curser and on Windows click or click on the start icon and type 'services', then click the services app.
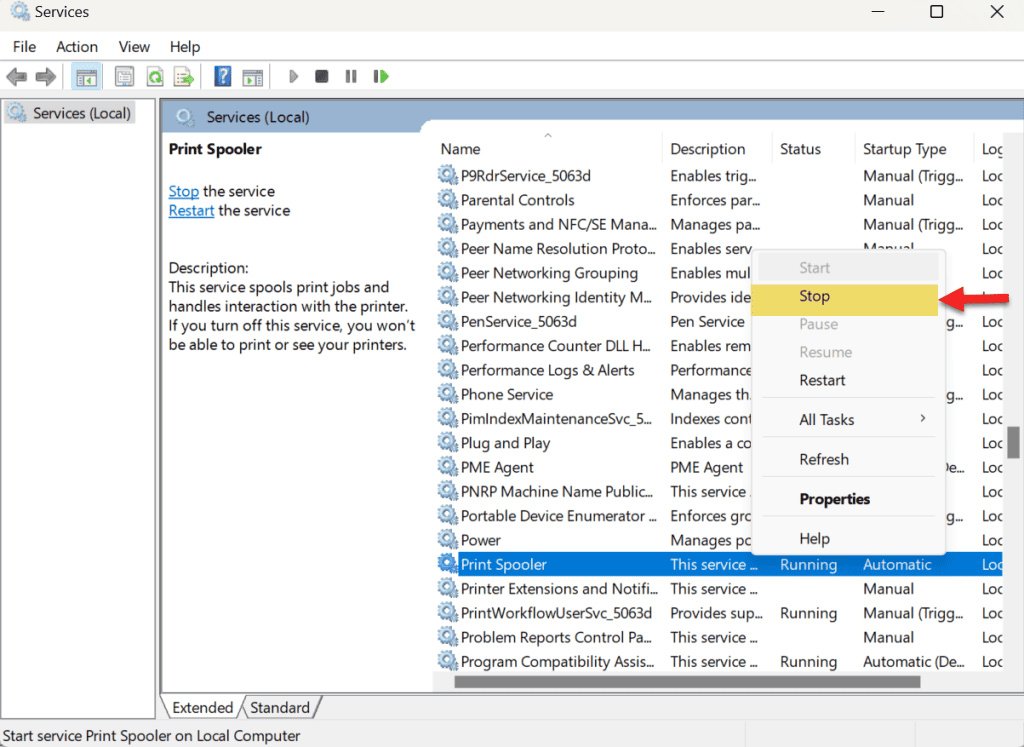
2. Locate 'Printer spooler' in the list and right-click it. Then click 'stop' and wait for 30 - 60 seconds.
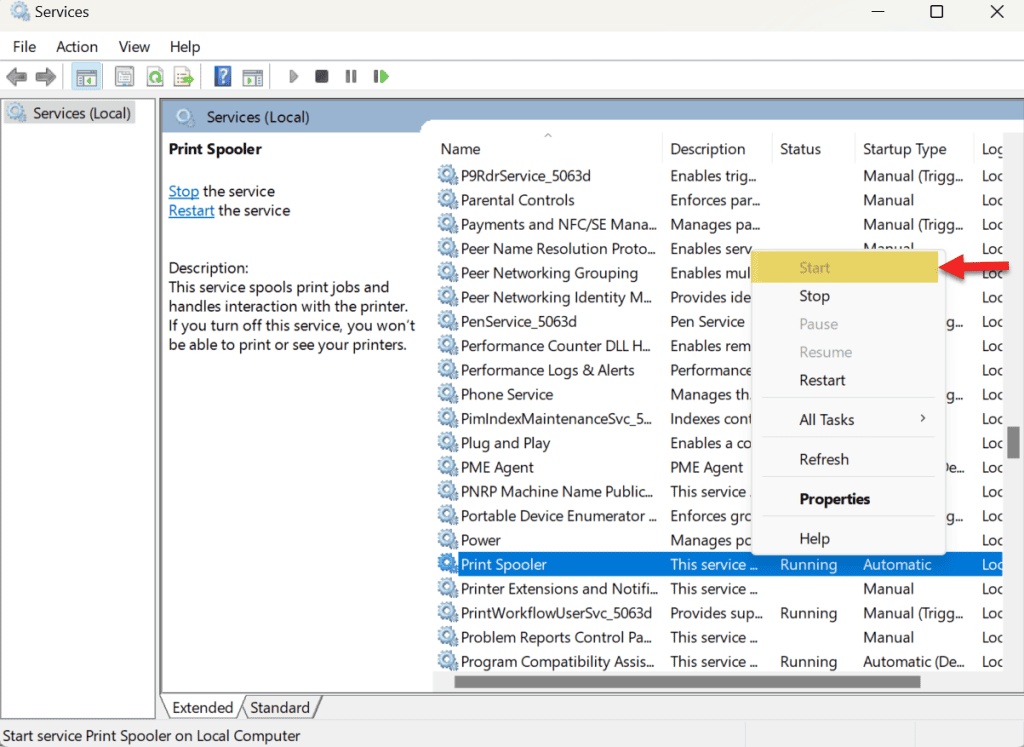
3. Right-click 'printer spooler' again and click 'start'
How do I clear the spooler in Windows?
The Spooler is a unique process responsible for coordinating printer access among multiple users. For the majority of users, the Spooler operates in the background, handling print jobs seamlessly.
The Spooler performs two primary functions:
- It spools print jobs by directing the output from a user’s process to a print file, concurrently creating an entry in the print queue for the job.
- It removes print jobs by clearing the print queue one job at a time for each printer as the assigned printer becomes available.
To clear the print spooler follow these instructions. This will allow you to clear your printer queue in a Windows OS:
- Go to Start.
- Click the Control Panel and look for Administrative Tools
- Double-click the Services icon.
- Scroll down and select the Print Spooler service.
- Select Stop.
Important Note: Make sure that you are logged in as the administrator. - Go to the following directory: C:\WINDOWS\System32\spool\PRINTERS. As an alternative option in case the C drive isn't configured as the default Windows partition, you can also type it into the address bar on your Internet browser.
- Delete all the files in this folder. This step will clear all print queues.
Critical Reminder: When executing this step on a server, verify that no other print jobs are in progress simultaneously.
Print Spooler vulnerability
Print Spooler poses a significant risk, acting as a potential entry point for attackers to compromise systems by exploiting weaknesses in print job management. Below are the most known Print Spooler vulnerabilities:
SpoolFool (CVE-2022-21999) Windows Print Spooler Elevation of Privilege Vulnerability
To create folders within the printer spool driver directory and load DLL files arbitrarily, the SpoolFool vulnerability alters the path of a printer port. This bypasses security checks present in previous print spool privilege escalation vulnerabilities.
(CVE-2022-38028) Windows print spooler vulnerability for Elevation of Privilege
CVE-2022-38028 is marked as critical by Microsoft. If this vulnerability is exploited then an unknown component of Windows Print Spooler is affected. In return, there is a loss of integrity, availability, and confidentiality. To mitigate this critical vulnerability a patch must be applied immediately.
Print Nightmare
Print spooler nightmare is a vulnerability that exists wherein a domain user, following authentication on the remote system, can execute code remotely on a Microsoft Windows system with the privileges of the local SYSTEM user. This issue, along with the corresponding patches and solutions released by Microsoft, is collectively identified as “PrintNightmare.” Print nightmare CVE is CVE-2021-1675, CVE-2021-34527, and CVE-2021-34481.
CVE-2021-36958 Microsoft zero day vulnerability
It is labeled as a Remote Code Execution threat, encompassing both Remote Code Execution (RCE) and Local Code Execution (LCE) vulnerabilities. This means that code needs to be fetched from a remote server before being executed on the local workstation.
Disable Print Spooler
In recent years, vulnerabilities in the Print Spooler have surfaced and it's recommended for a print nightmare fix as well as for the rest of the vulnerabilities to have it disabled. The Cybersecurity and Infrastructure Security Agency (CISA) recommends that administrators deactivate the Windows Print Spooler service on Domain Controllers and systems that do not require printing.
To minimize attack surface:
- Consider using non-Microsoft Print Spooler services to replace the vulnerable protocol.
- Restrict users' and drivers' access to the Print Spooler only to groups that must use it, by changing 'Allow Print Spooler to accept client connections'.
- Disable Print Spooler caller in Pre-Windows 2000 compatibility group.
- Make sure that Point&Print is not configured to No Warning - check registry key SOFTWAER/Policies/Microsoft/Windows NT/Printers/PointAndPrint/NoElevationOnInstall for DWORD value 1.
- Turn off EnableLUA - check registry key SOFTWARE/Microsoft/Windows/CurrentVersion/Policies/System/EnableLUA for DWORD value 0.
Here are the Best Practices for security configuration:
Disable if not needed
- If printing functionality is unnecessary on a system, consider disabling the Print Spooler service to reduce the potential attack surface.
- This can be accomplished using either the Services Management Console or Group Policy settings.
Restrict access
- By default, limit access to the Print Spooler service, as all users, including authenticated users, possess the capability to install print drivers and control print jobs. This precaution helps mitigate a security risk that attackers might exploit to gain unauthorized access to your system.
Harden Point and Print settings
- The Point and Print feature enables users to install print drivers automatically, bypassing the need for administrator privileges. However, this convenience poses a security risk by potentially allowing attackers to install malicious drivers.
- Strengthen Point and Print settings by utilizing Group Policy or Local Security Policy to mandate administrator approval for driver installations, enhancing overall system security.
Harden Inbound remote printing
- While enabling inbound remote printing offers convenience, insufficient configuration may introduce security vulnerabilities, opening the door to potential malicious attacks. Furthermore, it can result in performance issues such as slower printing and dropped jobs.

Security configurations for hardening
Ensuring the safety of your systems is like putting a digital shield around your printer empire. With the Print Spooler service in Windows managing the print jobs, hardening the Print Spooler service is crucial to mitigating the above vulnerabilities. Here are several hardening security configurations from the CIS Benchmarks:
- Ensure ‘Print Spooler (Spooler)’ is set to ‘Disabled’ (DC only) (Automated): This service spools print jobs and handles interaction with printers.
- Ensure ‘Print Spooler (Spooler)’ is set to ‘Disabled’ (MS only) (Automated): This service spools print jobs and handles interaction with printers.
- Ensure ‘Allow Print Spooler to accept client connections’ is set to Disabled’: This policy setting controls whether the Print Spooler service will accept client connections.
A hardening automation tool identifies locations with enabled Print Spooler, highlights areas requiring security configuration, and automatically disables or reconfigures them based on your chosen course of action.