The DoD or Department of Defense of the United States of America implements the CMMC or Cybersecurity Maturity Model Certification to standardize or normalize the overall preparedness for cybersecurity across the DIB (Defense Industrial Base) of the federal government against evolving threats.
What is a Maturity Model?
Maturity models are regarded as a collection of best practices provided by CMCC in order to protect the Federal Contact Information (FCI), Controlled Unclassified Information (CUI) and Department of Defense (DoD) information from breaches and vulnerabilities. Certification to a maturity model will imply that an organization or company has committed itself to enhancing the practices and processes within the domains of the model to a measured, sustainable level of top-class performance.
Understanding CMMC Certification
CMMC is a dedicated program that has been initiated by the DoD (Department of Defense) in the USA to measure the capabilities, sophistication, and readiness of the defense contractors in areas of cybersecurity. The framework can be regarded as a set of processes and input from existing cybersecurity standards -including DFARS, FAR, and NIST.
Importance of CMMC
It is believed that cybercrime is responsible for draining around $600 billion every year from the global GDP. Dependence on a huge network of contractors for executing the mission implies that the DoD will be entrusting every one of them with sensitive data that will effectively increase the overall risk profile of the Defense Industrial Base (DIB).
The DoD has a sense of outsize proportion and the burden of risks that cybercrimes tend to put on the base of sub-contractors. Most of these sub-contractors are small businesses; therefore, they might lack proper resources of their counterparts.
Due to this, the DoD went ahead with releasing the CMMC to facilitate the adoption of best processes with respect to cybersecurity with the 'Defense in Depth' strategy across the board for contractors throughout the globe.
Both versions of CMMC were focused on protecting CUI, however, the new scoping guidance for CMMC 2.0 makes it clear how to scope your environment. CMMC 2.0 also introduces the concept of waivers for certain mission-critical work. Such waivers will be strictly time-limited and may only be approved by senior DOD personnel.
Understanding the CMMC 2.0 Framework and Levels
The original CMMC program was introduced on 31st January 2020 and consisted of five tiers of maturity that required a company to master all the practices in one level before moving to the next. The Levels are:
Level 1: Basic
Level 2: Intermediate
Level 3: Good
Level 4: Proactive
Level 5: Advanced
CMMC 2.0 issued in November 2021 builds upon the initial CMMC framework to enhance Defense Industrial Base (DIB) cybersecurity against evolving threats and allow organizations to self-assess their programs rather than submit to third-party reviews.
The new levels of 2.0 are:
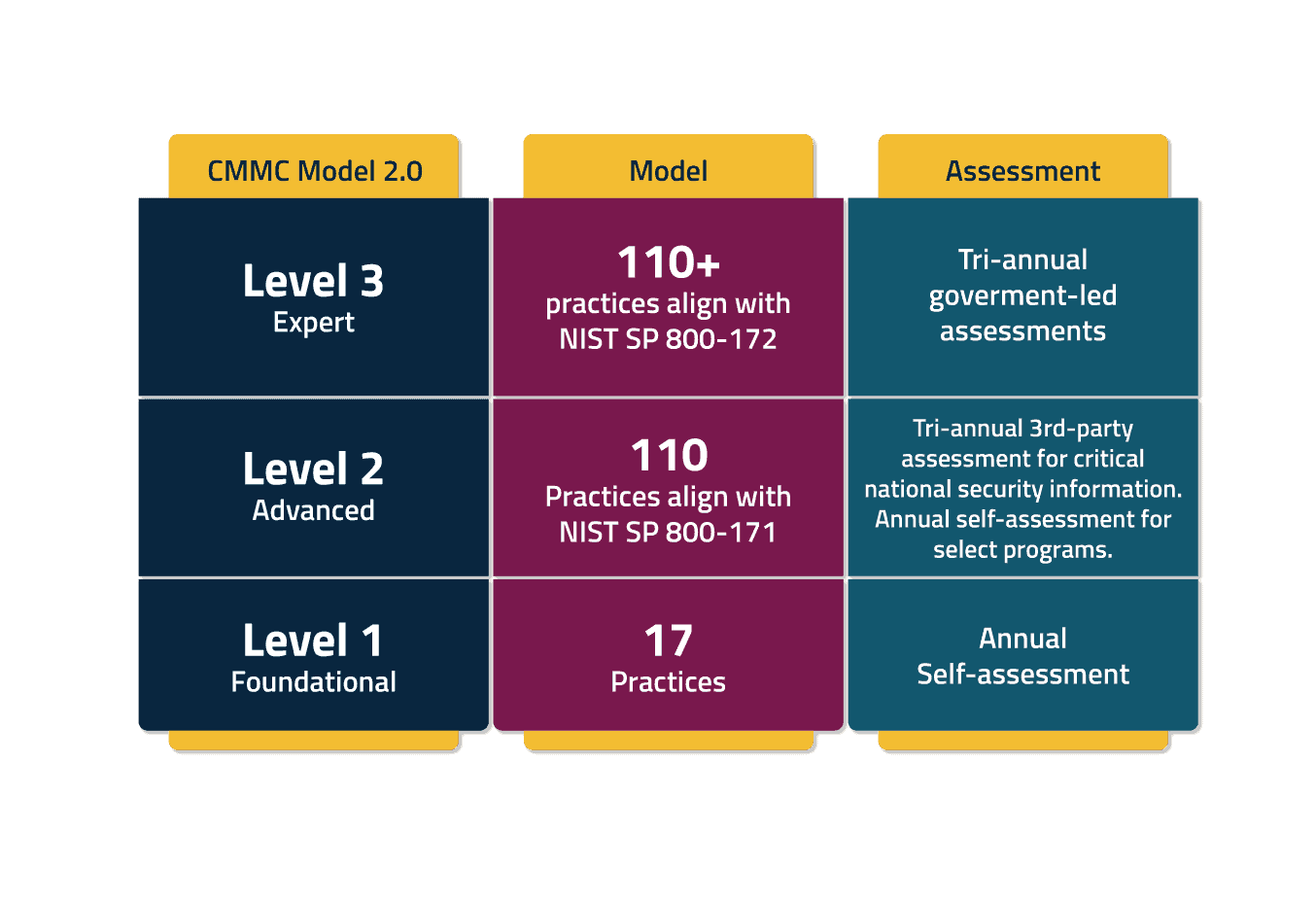
Level 1: Foundational
Requires annual self-assessments. 17 practices
Level 2: Advanced
Requires Tri-annual third-party assessments for critical national security information. Annual self-assessment for select programs. Aligns with NIST SP 800-171
Level 3: Expert
Requires Tri-annual government-led assessments. Aligns with NIST Special Publication 800-172
The primary motive of CMMC is ensuring protection of important information from unauthorized use or disclosure, including:
- CUI or Controlled Unclassified Information
- FCI or Federal Contract Information
It is estimated by 2026 all new DoD contracts will contain the CMMC requirements.
Takeaways and Look at Protection Strategies
CMMC incorporates 17 technical domains, 14 originate from the already established Federal Information Processing Standards (FIPS) 200 and NIST SP 800-171. Organizations that must implement NIST 800-171 requirements require establishing and maintaining security configuration settings for IT systems.
One of the 17 domains in CMMC is Configuration Management. Configuration Management states an organization must establish and maintain baseline configurations and inventories of organizational information systems. This includes software, firmware, hardware and documentation throughout the respective system development life cycles and enforce security configuration settings for information technology products employed in organizational information systems.
Addressing the specific framework of the CMMC 2.0 might impose new challenges for organizations wanting to achieve the baseline requirements. The CalCom Hardening Solution (CHS), can automate the baseline hardening configurations and implement the desired policies built to address CMMC requirements to comply with best practices mentioned above.